TLS protocols and their relative encryption suite (Cipher Suite) evolved and more recent solutions have adopted more enhanced and secure standards. Dated protocols (in particular TLS 1.0 and TLS 1.1) are considered unsafe and are nowaday deprecated.
Legacy clients might still use deprecated version of TLS in their firmware/software and try to connect to services that have to support advanced standards and block the old ones to ensure the overall security.
From ThinMan version 8.5.2 it is possible to choose the desired web services security level regarding TLS protocols and Cipher Suite. The option is allowed only to the ThinManRoot user and is available only with ThinMan Advanced license. The security level determines the enabled TLS protocols, allowing connection from deprecated versions of the standard or forcing the use of only the currently secure ones.
¶ Web services and ThinMan
On the ThinMan server, web services are used mainly to:
- Expose the web console.
- Connect to the ThinMan remote console.
- Connect to the Thinman Gateway.
- Manage the Secondary Thinman.
- Expose the services for the status synchronization and management of the devices (HTTP, HTTPS, WSS protocols).
¶ Selecting enabled TLS protocols (and Cipher Suites) from the console
Go to the menu Tools -> Security Endpoint Communication - TLS Protocols settings.
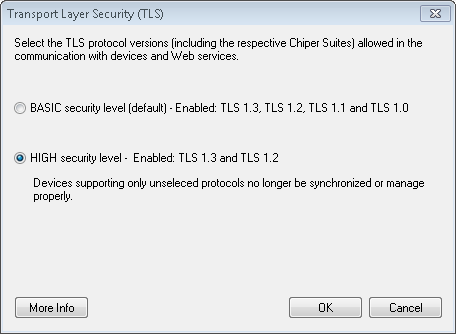
In order to balance the requirements of security and backwards compatibility 2 possible levels are available, each enabling different sets of TLS protocol versions (and the respective Cipher Suites) as shown in the table below.
| Level | TLS | Cipher Suite | Device full compliant | Device non compliant |
|---|---|---|---|---|
| High | 1.3 1.2 |
TLS_AES_256_GCM_SHA384, TLS_AES_128_GCM_SHA256, TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384, TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256, TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384, TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256, TLS_DHE_RSA_WITH_AES_256_GCM_SHA384, TLS_DHE_DSS_WITH_AES_256_GCM_SHA384, TLS_DHE_RSA_WITH_AES_128_GCM_SHA256, TLS_DHE_DSS_WITH_AES_128_GCM_SHA256, TLS_EMPTY_RENEGOTIATION_INFO_SCSV |
ThinOX and ThinOX4PC version >= 11.1 ThinClient W10 IoT all editions Devices running Agile4PC Agile4Pi |
ThinOX and ThinOX4PC version < 11.1 will no more manageable: Stutus not synchrnozid, not presented anymore as HTTPS-Linked/Unlinked, no more reachable/manageable WES 7 devices: Capture/Apply Windows Image will no more properly managed WE 8, WinXPe, CE devices: no more properly managed |
| Basic (default option) |
1.3 1.2 1.1 1.0 |
TLS_AES_256_GCM_SHA384 TLS_AES_128_GCM_SHA256 TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384 TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256 TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 TLS_DHE_RSA_WITH_AES_256_GCM_SHA384 TLS_DHE_DSS_WITH_AES_256_GCM_SHA384 TLS_DHE_RSA_WITH_AES_128_GCM_SHA256 TLS_DHE_DSS_WITH_AES_128_GCM_SHA256 TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 TLS_DHE_RSA_WITH_AES_256_CBC_SHA256 TLS_DHE_DSS_WITH_AES_256_CBC_SHA256 TLS_DHE_RSA_WITH_AES_128_CBC_SHA256 TLS_DHE_DSS_WITH_AES_128_CBC_SHA256 TLS_ECDH_ECDSA_WITH_AES_256_GCM_SHA384 TLS_ECDH_RSA_WITH_AES_256_GCM_SHA384 TLS_ECDH_ECDSA_WITH_AES_128_GCM_SHA256 TLS_ECDH_RSA_WITH_AES_128_GCM_SHA256 TLS_ECDH_ECDSA_WITH_AES_256_CBC_SHA384 TLS_ECDH_RSA_WITH_AES_256_CBC_SHA384 TLS_ECDH_ECDSA_WITH_AES_128_CBC_SHA256 TLS_ECDH_RSA_WITH_AES_128_CBC_SHA256 TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA TLS_DHE_RSA_WITH_AES_256_CBC_SHA TLS_ECDH_ECDSA_WITH_AES_256_CBC_SHA TLS_ECDH_RSA_WITH_AES_256_CBC_SHA TLS_ECDH_ECDSA_WITH_AES_128_CBC_SHA TLS_ECDH_RSA_WITH_AES_128_CBC_SHA TLS_RSA_WITH_AES_256_GCM_SHA384 TLS_RSA_WITH_AES_128_GCM_SHA256 TLS_RSA_WITH_AES_256_CBC_SHA256 TLS_RSA_WITH_AES_128_CBC_SHA256 TLS_EMPTY_RENEGOTIATION_INFO_SCSV |
All devices are supported |